How serious is the cyber threat?
According to the World Economic Forum, cyber attacks rank third out of the 10 most likely risks threatening humanity, ahead of large scale migration (sixth) and terrorist attacks (eigth). Indeed, the probability of experiencing a cyber attack is currently one in four.
What are the greatest cyber risks?
There are a wide range of risks including: client data breaches, internal hacking, ransomware, phishing attacks, computer viruses, cryptocurrency hijacking and DDoS — distributed denial of service attacks via botnets. 48% of cyber attacks are criminal or malicious attacks. The top assets targeted are databases (servers) at 20% and POS terminals (user devices) at roughly 18%. Personal data, at 40%, and payment data, at 35%, are most often compromised. The average cost of resolving one record hacked is US$157.
How much is being spent on cyber security?
Cyber security is growing fast and expenditure is expected to grow to US$170 billion by 2020 from US$3.5 billion in 2004. While it has been jumping to catch up with cyber crime, it has not succeeded in curbing cyber damages which are currently estimated at topping US$2.1 trillion in 2018 and reaching US$2.5 trillion by the end of 2020. Asean countries alone suffered losses of US$750 billion.
What is the available coverage for cyber insurance?
Insurance companies seem to be lagging behind in valuing cyber risks and thus providing differentiated coverage. The maximum cyber coverage available for each firm is only US$300 million. A breach involving 50 million records costs an average of US$350 million.
The value of the overall insurance market is expected to grow to US$4.6 billion in premiums by 2023. The relatively small volume in relation to the size of the risk is in part due to insurance companies not yet coming to grips with how to value cyber risks in dollars and cents. The cyber field and finance are not truly in sync yet. C-level executives in companies are hard pressed to squeeze financial data about risk and return out of their technically oriented IT teams.
What are the advantages of valuing cyber risk?
Putting detailed financial risk numbers to cyber risk will help grow the cyber liability risk business for insurers and reinsurers. Although cyber liability insurance is developing, it is well behind where it should be, partly because insurers cannot accurately quantify cyber risks. In addition, the shear dimensions of cyber damages are overwhelming — these damages are often hard to quantify in final terms. For example, what is the impact of a cyber attack on the equity value of a company? The only costs currently being considered are immediate expenses.
Financially quantifying cyber risks allows insurers to adjust premiums, select insurable cyber risks rather than others, and thus drive their cyber insurance business.
What can be done to help insurers come to grips with cyber risks?
Insurers wear two hats in the cyber world. First, by offering cyber liability coverage, and second, by themselves being major targets of cyber attacks. Insurers harbour the data of billions of people on a worldwide scale. They hold the type of data which is most likely to invite cyber attacks.
Thus, insurers are fighting cyber crime on both fronts. It is therefore important they use methods which enable them to quantify the total and changing risk exposure of themselves and their clients to cyber threats. They should ask: what is my total risk exposure right now? What is my risk in terms of costs (for example lost productivity, litigation and regulatory fines) and in terms of the value of my company? And which is the best way to capture all these risks in a single metric, such as a discount rate?
How accurately can you assess the value at risk and how?
Financial executives use discount rates to quantify the general risk exposure of their companies. These rates are used to discount future cash flows to a net present value and functions as a metric to value a unit or company. With cyber growing to a major threat to the operations and value of a company, it should be added a component of the corporate discount rate.
Value at Cyber Risk (VaCR) is developed by Management & Excellence and offered in Hong Kong with Moore Stephens; it quantifies all cyber risks at any one time in terms of a cyber discount rate. With VaCR, all cash flows and the company’s value can be discounted using this rate. Even more importantly, VaCR calculates cyber risks as they fluctuate. If, for example, a company institutes a new measure to combat cyber breaches, VaCR can adjust the risk level in the company accordingly.
Insurers benefit doubly from VaCR: they can better structure cyber liability insurance and can assess/improve their own cyber risk exposure.
What is a cyber threat assessment?
This involves undertaking a complete technical, strategic and financial review of the areas of a company which determine its cyber risk level; from IT systems to its governance and HR policies. Roughly one-third of cyber breaches can be traced to current and former employees and suppliers. Negligence is a major source of cyber risk. A good cyber threat assessment will also involve tapping into world data flows and measuring the sources and levels of specific threats to a company. Only highly developed cyber specialists have access to these data flows.
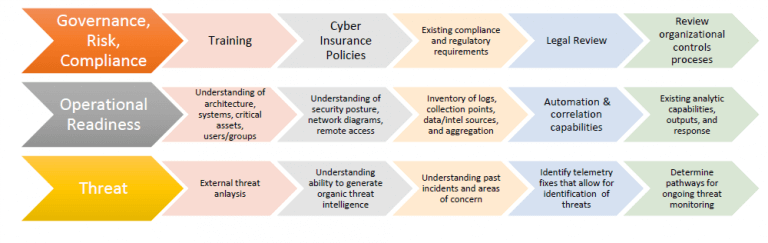
What does a cyber threat turnaround strategy involve?
This involves a range of tasks including: integrating enhancements into the collection, aggregation and correlation capabilities to increase data accuracy, consistency, visibility or analytic capabilities.
In addition: upgrading or altering cyber insurance policies to account for increased risk; automating manual processes that support data collection or analytics to improve the timeliness, normalisation and consistency of data processing.
Other methods involve: generating improved incident response playbooks; identifying new training methods or sources; tightening the integration of data sources into the data processing pipeline to improve context, priority, and filtering.
Noise reduction and data labeling should be used where possible, for example scanning devices, back-up activity, and trusted external or cloud connections; there are quick wins filling gaps within the current capability, for example rules, signatures and dashboards to improve collection, visibility or capability to aid the company’s threat intelligence and hunt teams.
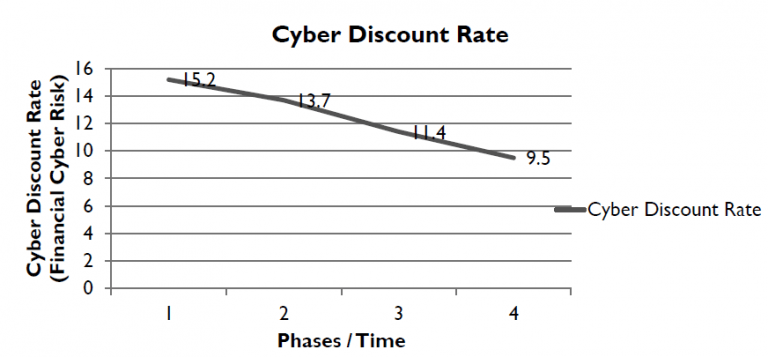
Can you monitor cyber threats in real time?
Yes. In essence this involves translating technical and organisational data into financial data which are expressed in a VaCR cyber discount rate. This rate should be declining as the turnaround strategy takes effect:
This article was written by William Cox , chief executive of Management & Excellence, which is based in Madrid and New York.
-
IFRS 17: Making your financial controls automation truly work for you
- September 26
Shifting towards a more automated and streamlined workstream can free up time for insurers to critically analyse results that inform future financial planning.
-
Flood resilience: Water, water everywhere…
- September 11
Floods are one of the most complex natural perils with highly localised impacts, making them challenging to insure and data is key to the effective design of an affordable product to protect the vulnerable.
-
Maritime energy transition: Data dialogue key to achieving decarbonisation goals
- August 3
Collaboration and shared learning amongst stakeholders will be vital to getting full value from the data captured as well as in achieving regulatory goals. The International Maritime Organisation’s (IMO) greenhouse gas (GHG) strategy is to reach net-zero emissions from international shipping by or around 2050, and there are various checkpoints to meet along the way. […]
-
Contentious losses: Evidence-led forensic investigations stand the test of time
- May 17
Even minor cracks in evidence capture will become exposed when it comes to recovery and repudiation. Forensic investigations form part and parcel of many insurance claims in the Asia-Pac region. Whether a loss is complex, costly, or if there are expected to be questions down the line around causation and liability, insurers and their loss […]
-
HSBC Asset Management | The hunt for diversification and performance revitalizes appetite for Asian currency bonds
With diversification and performance high on investors’ agendas, it seems a good time for global portfolios to revive allocations in Asian local currency bonds – including Hong Kong dollar (HKD) bonds.
-
PineBridge Investments | Why Asian insurers are exploring private credit and CLOs
The recent rollout of risk-based capital regimes across Asia calls for a closer alignment between insurers’ assets and liabilities. We explore potential ways to maintain a healthy investment yield and robust returns on regulatory capital.
-
Peak Re | Emerging Asia middle class: A catalyst for change
Rising demand for elderly care and women driving consumption growth mandate carriers to develop precise solutions to meet customer expectations.
-
Guy Carpenter | Private equity’s reshaping of the Asian life sector has further to run
PE-backed reinsurers provide access to asset classes and investment expertise that often don’t exist within the traditional carriers themselves.

William Cox, Management & Excellence
Evaluating the cyber risk threat
William Cox, Management & Excellence